So what is the solution? Certainly commercial firewall solutions would be the best choice if you had a lot of money, but do you have a $5000 in your yearly firewall budget? I don't, and that's why I take an old Pentium machine with 32MB RAM and a 1Gb HD and make it the masquerading firewall.
The Iptables can be a little bit confusing to understand and I certainly recommend some thorough understanding of TCP/IP before you read on. Check my website for networking books that I recommend. It took me quite a while until I had a grasp on the Iptables and I will try to pass that on to you. Don't let configuration files scare you, at first glance they look very confusing (like most things on Linux if you're not used to them) but turn out to be quite tame once you understand them. I will use a simple but hopefully helpful example to explain iptables. Some basics now:
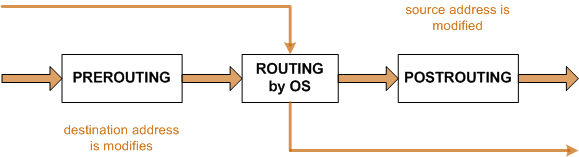
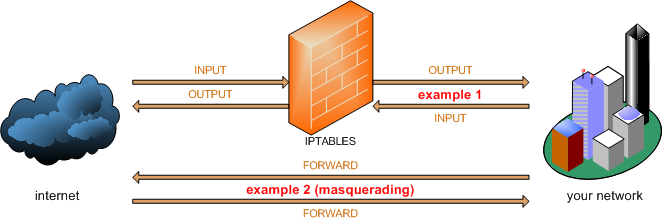
Our beloved iptables use several so-called chains to configure its behavior: INPUT, OUTPUT, FORWARD and for NAT: PREROUTING and POSTROUTING.
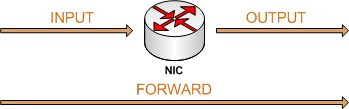
We will then apply rules to those chains to customize and control the behavior of our Linux Bastille.
Please note that, without mentioning it again in the examples later, I assume that all traffic has been disallowed by using –F chain and –P chain DROP, example:
|
iptables –F INPUT
|
# FLUSH THE INPUT CHAIN (remove all rules)
|
|
iptables –P INPUT DROP
|
# SET THE DEFAULT POLICY TO DROP
|
|
iptables -F OUTPUT
|
# FLUSH THE OUTPUT CHAIN
|
|
iptables –P OUTPUT DROP
|
# SET THE DEFAULT POLICY TO DROP
|
|
iptables –F FORWARD
|
# …
|
|
iptables –P FORWARD DROP
|
# …
|
The above lines need some explanation. As already stated we apply rules to the existing INPUT, OUTPUT or FORWARD chains. Whenever we configure our box I want to make sure that the chains are empty since rules will be followed step-by-step.
The –F switch accomplishes this by removing all rules of a specific chain, lines 1,3 and 5 are explained.
The –P switch on the other hand sets the default policy for a chain. Right after we flush the chain it is empty, packets will not match a single rule since there aren't any rules. A default policy of a chain can either be ACCEPT or DROP and I prefer DROP. This means that every packet that has arrived at the end of a chain will be matched against the default policy, DROP in the example above. It is usually more secure to deny everything that has not been explicitly allowed.
Additionally we want to set up environment variables to make our script(s) easier to maintain:
EXT_IFACE="eth1"
LAN_IP="172.24.10.0/24"
Example 1:
Let's imagine a simple example, we set up a host and only want it to accept http connections since this is the only service that should be accessed. Of course we already deactivated all services, but additionally we want to allow only TCP packets that were sent to the local port 80. Clearly this will be configured on the input chain since we are talking about an incoming packet. Good, now since our remote http client would probably appreciate some kind of feedback, we also need to allow packets leaving the interface, via the output chain. Of course we don't want any packet to leave the output chain, since an intruder could use that to his advantage and send data from our host, no matter if that is a Trojan horse or a simple ftp client. The iptables have a very nice feature as they now support the statefulness of packets, by using –m state –state ESTABLISHED, RELATED. Sounds good, it sure is! If we could actually talk to iptables (maybe in the 4.14 kernel?) we would say:
- Allow all packets that are TCP and are sent to port 80 on this interface.
- Allow all packets that refer to a previous packet ( -ESTABLISHED) or to an existing connection (like ICMP replies, FTP data sessions …, -RELATED) to leave the interface.
All other packets would be denied since they were not specifically allowed. This is the "code":
iptables –A INPUT –p TCP -–dport 80 –i eth0 –j ACCEPT
iptables –A OUTPUT –p TCP –o eth0 –m state -–state ESTABLISHED –j ACCEPT
Line 1:
|
-A INPUT
|
means that we want to configure the input chain
|
|
-p TCP
|
refers to only TCP packets (and not UDP packets)
|
|
--dport 80
|
matches only packets that were sent to port 80
|
|
-i eth0
|
applies only to the eth0 interface
|
|
-j ACCEPT
|
jumps to the ACCEPT target, hence lets the packet pass
|
Line 2:
|
-A OUTPUT
-p TCP -o eth0 -m state --state ESTABLISHED -j ACCEPT |
packets leaving our interface
TCP only packets leaving interface eth0 specify a state only related packets are allowed, not new connections let the packet go trough |
Example 2:
This might be a little bit more complicated than the previous example. We just set up our new DSL line and are mighty happy, except for one thing: We are only supposed to use one computer to connect to the internet! Dang, how boring! Of course we have several computers around that all want to connect to the Internet which at this point doesn't work. I always feel a little badly to fool my ISP who, in endless generosity, has granted me the privilege to connect to the Internet in such high speed. Yet I really only use one computer at the time to connect to the Internet, but from different machines.
In plaintext, we need a firewall that supports IP masquerading. No problem for the iptables since they support connection tracking. Now what is exactly that we want?
- All packets originating from our internal LAN should be sent to the correct host on the Internet; all packets coming from the Internet that relate to a connection that was initiated previously from the internal LAN should be allowed to enter our network.
- Additionally, the ip headers need to be modified by iptables so that our firewall appears to be the requesting and receiving host, instead of our machines in the LAN that probably have ip addresses not even valid on the Internet (10.0.0., 172.24.0.0, 192.168.0.0).
That's what we call masquerading. Iptables accomplishes this by keeping track which host (from the LAN) requested which connection, and by subsequently, upon arrival of the response (from the Internet), sends the packet back to the internal host. Puh, cool stuff.
This is the first example where we need to look at another chain, the FORWARD and POSTROUTING chain. I found the POSTROUTING (and PREROUTING) chain a little confusing, so read the following if you find it confusing too.
Let's forget the iptables stuff for a while and think of our Linux box as a plain router. We have our little LAN, and we have the endless space of the Internet. To send packets from our internal LAN we need to route the packets through our Linux box. So if we request http://www.netikus.net