In this example, one is notified of important events through a SMTP target. Incoming Syslog messages from host 10.10.10.50 are logged to a FILE target, and entries from the security event log are sent to a Linux host with IP address 10.10.10.15.
1. Setting up the syslog daemon
To activate the EventSentry syslog daemon we check the Enable checkbox in the main configuration screen
and click on Configure. In the Configure Syslog Options window add the IP address 10.10.10.50 to the list of allow remote syslog hosts and set the Error Level Mappings and Threshold Settings as shown in the screenshot below. For more information on the syslog daemon configuration see "Configuring Syslog".
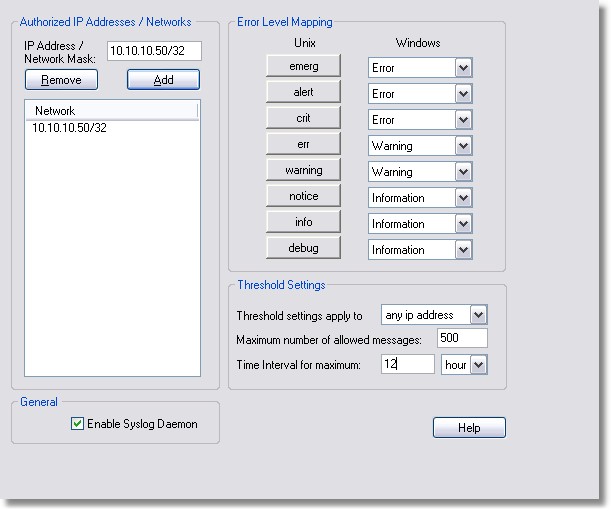
Please note that the Error Level Mappings and Threshold Settingsare only suggestions and can be changed.
After setting up the syslog daemon we will setup the targets and filters.
2. Add an SMTP Target
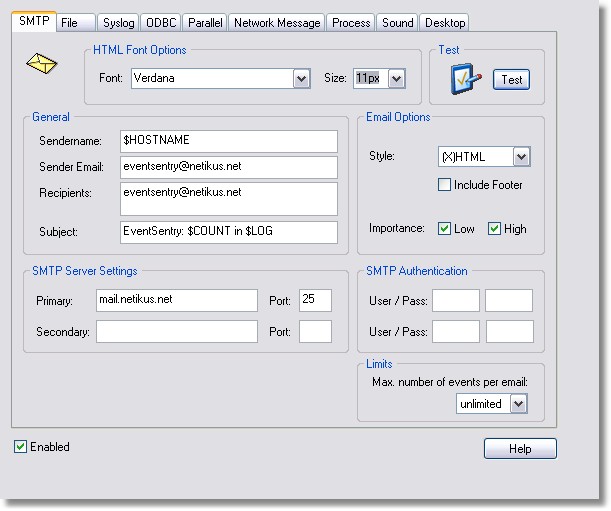
All filters that are going to use this target will send event log entries through the mailserver mail.netikus.net sent from eventsentry@netikus.net to eventsentry@netikus.net.
3. Add a FILE Target
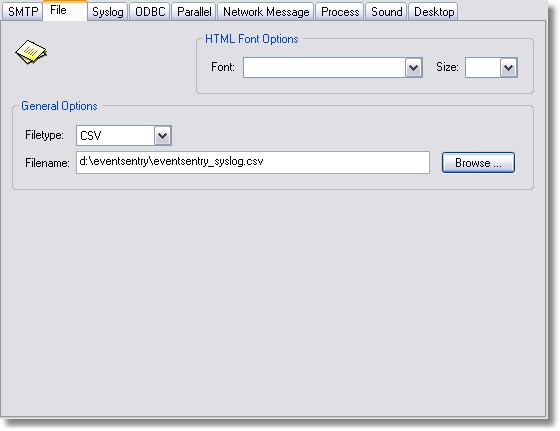
All filters that are going to use this target will log event log entries to the file d:\eventsentry\eventsentry_syslog.csv.
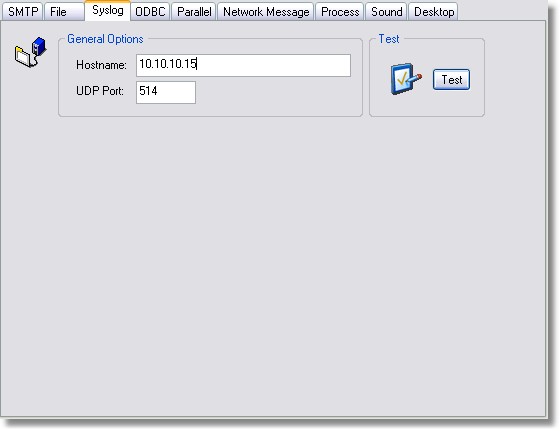
4. Add a Syslog Target
All filters that are using this target will send event log entries to host 10.10.10.15.
The "Installed Targets" list should then look like this (the order is not relevant):
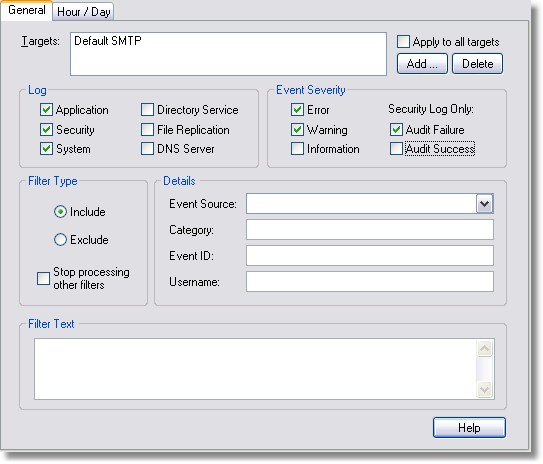
5. Add an Include Filter for the SMTP Target
This filter will log Warning, Error and Audit Failure event log messages from the Application, Security and System event log to the target SMTP Target.
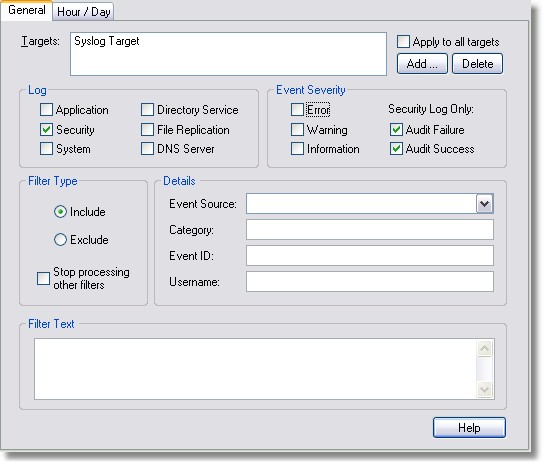
6. Add an Include Filter for the SYSLOG Target
This filter will send all entries from the Security event log to the host defined in target Syslog Target.
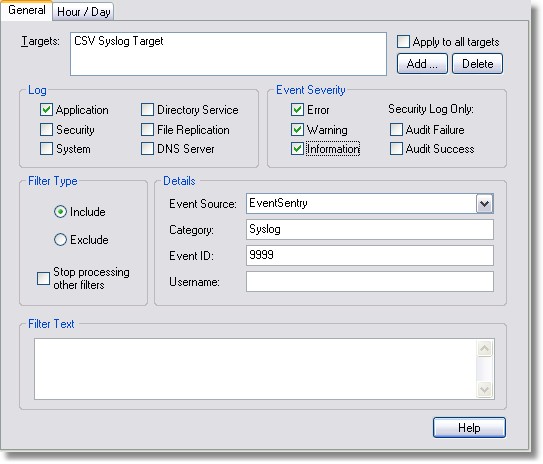
7. Add an Include Filter for the FILE Target
This filter will write all entries logged by the EventSentry syslog daemon to the file specified in the CSV Syslog Target. Since all messages logged by the EventSentry syslog daemon come from the source EventSentry with event ID 9999 and event category "Syslog" (see the Syslog chapter) we will need to configure the filter accordingly.
This completes the configuration and the Installed Filters list should look like this:
Since all filters are include filters, the order in which the filters are arranged does not matter. If you were to add an exclude filter in this example you would need to make sure that the exclude filter appears before (=above) the include filter it should exclude from.